Published On Dec 11, 2023
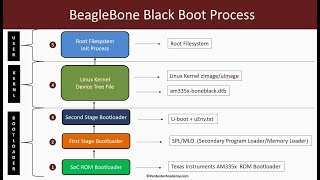
Uboot is arguably the defacto standard for providing adaptable bootloader environments for a plethora of infrastructures. Unfortunately some of the configuration options may expose vulnerabilities which compromise environments and may allow attackers to take control during privileged contexts. The talk included here will cover some of the Uboot basics, detail some architectural aspects of modern bootloaders as well as ways an eager hacker can exploit Uboot in order to drop a shell and take control.
Bootloaders are an obscure part of the operating system, they load the operating system, setup up the hardware and present us with a working, running machine all out of sight and out of mind. Though seemingly hidden, a large aspect of the operating systems security depends on a secure chain of trust being established between hosting hardware and the bootloader stages. When developing an embedded platform engineers and security staff cannot take all that hidden magic for granted and are required to understand the pitfalls common to bootloaders. Additionally with the advent of UEFI and Trusted Computing Platforms the security and idiosyncrasies of the bootloaders and their supporting hardware have taken the spotlight.
In this talk, listeners will learn about the fundamentals of bootloader architecture, how a secure chain of trust is established as well as the common pitfalls in Uboot configurations. The talk will cover pin2pwn attacks, a few ways attackers can perform malicious modification of firmware and abuse of unsecured environment variables. In order to provide a full perspective of secure Uboot configuration the talk will work through some of the subtle configuration changes which disable boot prompts, boot delays and show some ways to ensure that secure boot is configured correctly.