Published On May 9, 2023
Join the Discord Server!
/ discord
---------------------
MY FULL CCNA COURSE
📹 CCNA - https://certbros.teachable.com/p/cisc...
FREE CCNA FLASHCARDS
🃏 CCNA Flashcards - https://certbros.com/ccna/flashcards
HOW TO PASS THE CCNA
📚 Get a great book - https://amzn.to/3f16QA5
📹 Take a video course - https://certbros.teachable.com/p/cisc...
✔ Use practice exams - https://www.certbros.com/ccna/Exsim
SOCIAL
🐦 Twitter - / certbros
📸 Instagram - / certbros
👔 LinkedIn - / certbros
💬 Discord - https://www.certbros.com/discord
Disclaimer: These are affiliate links. If you purchase using these links, I'll receive a small commission at no extra charge to you.
---------------------------------------------------------------------------------------------------------------
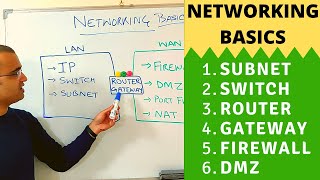
What is a DMZ?
Well, the name comes from the military.
In military terms, it's an area where military activity is forbidden, often along borders. A well-known example of a Demilitarised Zone is the border between North and South Korea.
A DMZ, in computer terms, is similar. It's an area of a network where security rules and policies are more relaxed.
But, why on earth would you want to relax security policies?
Well, imagine you have a web server. You install it in your network just like all of your other devices.
You want people to access your web server and visit your website right? So you allow public access to your web server through your router and firewall.
Great, so now people can come and browse your website, www.example.com, and the request will be sent to your web server sitting inside your network.
Now, this may seem fine, but it leaves you vulnerable to attacks. Web servers and websites are not bulletproof, and they require a lot of work to keep maintained, up-to-date and secure.
Let's say an attacker targets your website, and that attacker can get access to the web server itself. This is where the problems start.
Because our web server is installed alongside our other corporate servers and workstations, the attacker can now start to attack these machines from the web server. With a bit of luck, the attacker could gain access to the entire network. This is called lateral movement.
From here, it's really up to the attacker what they do next. It could be the exfiltration of your data or infecting your systems with ransomware, which will encrypt your data.
So, what is the solution?
Instead of installing the web server in the corporate network, we can install it into its own network called a DMZ.
A DMZ is created with two firewalls. The first firewall allows public access to our web server; the second firewall blocks public access.
If an attacker can access our web server, they may try to get lateral movement by attacking other machines in the network. Well, because we have separated this web server into its own network, there are no other machines to attack, and our second firewall blocks access to our corporate network.
So, while the web server has been compromised, the DMZ allows us to contain the attack to just that web server.
This dramatically reduces the cyber attack's impact and makes the hacker sad. Meanwhile, the rest of the corporate network is unharmed and operating as normal.